Wifi Security Modules:WEP, WPA, and WPA2
WEP, WPA and WPA2 are three popular types of network security modules used by the device. People get confused when it comes to using the security module on the network device. In such here is a detailed guide to all types of security models used on network devices. Their advantages, disadvantages, usage, feature and all. So, without further a dew let’s unlock the realm of Network security protocols and learn about WEP, WPA and WPA2 which may help you consider which one is better for you.
Wi-Fi security protocols: WEP vs WPA vs WPA2
Wifi security protocol is used to secure the network connection and protect the data from unauthorized access. A wifi connection is less secure as compared to a wired connection. In such wifi security modules come into place to help one to secure the network using a network security key.
The most commonly used Wi-Fi security protocols are WEP, WPA, and WPA2.
The wifi security modules use the cryptographic keys technology to randomize data to make it undecipherable.
All Wi-Fi security protocols are certified by the Wi-Fi Alliance, the non-profit organization that owns the Wi-Fi trademark. There are four wireless security protocols currently available:
- WEP(Wired Equivalent Privacy)
- WPA(Wi-Fi Protected Access)
- WPA 2(Wi-Fi Protected Access 2)
- WPA 3(Wi-Fi Protected Access 3)
Here is a detailed explanation of all the modules, including the usages, advantages and disadvantages.
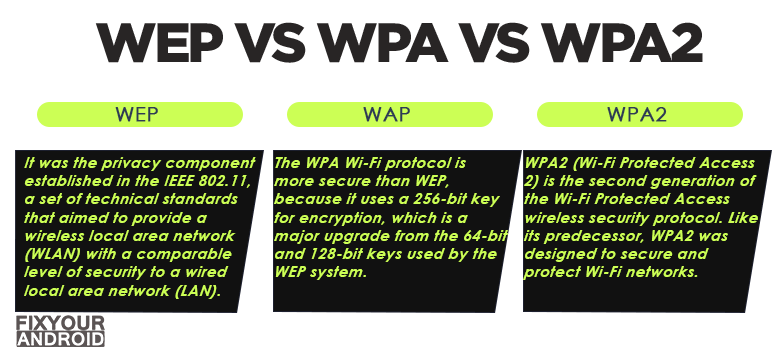
What is WEP (Wired Equivalent Privacy)?
WEP (Wired Equivalent Privacy) is the oldest and most commonly used wifi security protocol. Introduced in the year 1997, WEP was the first ever wireless security protocol. Along with the introduction of wi-fi technology on the network, the WEP came to the surface.
In other words, WEP (Wired Equivalent Privacy) was the primary wifi security protocol module introduced with first wi-fi network device.
The aim was to add security to wireless networks by encrypting data. If wireless data were intercepted, it would be unrecognizable to the interceptors since it had been encrypted.
WEP encrypts traffic using a 64-bit or 128-bit key in hexadecimal. This is a static key, which means all traffic, regardless of device, is encrypted using a single key.
The WEP key is nothing but a password you need to join the wifi network from your device. This key can be obtained either by asking from the network owner or simply can see the default WEP key printed on the back of your router.
Also, If you can’t determine the password on your router, you may be able to reset it.
A WEP key allows computers on a network to exchange encoded messages while hiding the messages’ contents from intruders. This key is what is used to connect to a wireless-security-enabled network.
Read Also: How to find network security key? Android, Mac, Windows
What is WPA (Wi-Fi Protected Access)
With flaws in the protocol, a more secure version of the wifi network security module was introduced as a replacement for WPE. Introduced in 2003 this protocol was called WPA(Wi-Fi Protected Access).
WPA(Wi-Fi Protected Access) is quite similar to WEP but with some improvements in it handles security keys and the way users are authorized.
It uses a 256-bit key for encryption, which is a major upgrade from the 64-bit and 128-bit keys used by the WEP system.
What is WPA 2(Wi-Fi Protected Access 2)
WPA 2(Wi-Fi Protected Access 2) is the most recent and second generation of Wi-Fi Protected Access wireless security protocol. With the same perspective of securing the connection and protecting the connection.
The major security update with WPS2 is the Advanced Encryption System (AES) that replaced the more vulnerable TKIP system used in the original WPA protocol.
AES provides strong encryption and is broadly popular and used by US government to protect classified data by securing the connection.
Unfortunately, like it’s predecessor, WPA2-enabled access points (usually routers) are vulnerable to attacks through WEP.
To eliminate this attack vector, disable WEP and, if possible, make sure your router’s firmware doesn’t rely on WEP.
The only notable vulnerability of WPA2 is that once someone has access to the network, they can attack other devices connected to the network.
This is an issue if a company has an internal threat, such as an unhappy employee, who hacks into the other devices on the company’s network.
Read Also: Ways To Receive Wifi Signal From Long Distance
What is WPA 3(Wi-Fi Protected Access 3)
WPA 3(Wi-Fi Protected Access 3) works on Perfect Forward Secrecy, an automated data encryption technology. However, this is more secure than it’s predecessor but not widely in use. Not by network devices not by smart devices.
As the most up-to-date wireless encryption protocol, WPA3 is the most secure choice. Some wireless APs do not support WPA3, however. In that case, the next best option is WPA2, which is widely deployed in the enterprise space today.
This new version will have, “new features to simplify WiFi security, enable more robust authentication and deliver increased cryptographic strength for highly sensitive data markets.” WPA3 is still being implemented so WPA3-certified hardware isn’t an available option for most people.
WEP vs WPA vs WPA2: The Differences
There are 3 types of wireless security protocols in use nowadays. All have their own advantages and flaws. Unlike WEP, WPA and WPA2 are the most common security measures that are used to protect wireless Internet.
Here is the comparison table that explains the differences between WEP, WPA and WPA2.
| Security Protocol | WEP | WPA | WPA2 |
|---|---|---|---|
| Year of Introduction | 1999 | 2003 | 2004 |
| Session key size | 64-bit/128-bit | 256-bit | 256-bit |
| Cipher type | RC4 stream cipher | TKIP (RC4-based) | AES |
| Data integrity | Cyclic Redundancy Check | Message Integrity Check | CCMP |
| Authentication method | Open system/Shared key | PSK | PSK + PMK |
| Key management | Symmetric key encryption | WPA + WPA-PSK | PMK + PSK |
| Encryption protocol | Fixed-key | TKIP | CCMP |
What’s the Best Wireless Internet Security Method?
Well, the wireless security protocol pretty much depends on the device you are using and the modules supported by the device. WEP, WPA and WPA2 are the popular modules available on most of devices nowadays.
If you have the option, here is the list of the best security protocols, ordered from most secure to least secure:
- WPA3
- WPA2 Enterprise
- WPA2 Personal
- WPA + AES
- WPA + TKIP
- WEP
- Open Network (no security implemented)
Why Would Someone Choose WPA?
Besides the weak security protocol and using the shorter password that makes the network vulnerable, the older device doesn’t support WPA2, as such you might need to rely on WPA.
However, isn’t an enterprise solution for WPA because it’s not built to be secure enough to support business usage. Still, it is a good choice to select WPA over WEP.
It also can be utilized with minimal processing power and could be a better option for you than the WEP alternative.
Why Would Someone Choose WPA2?
WPA2 uses AES encryption and long passwords, which make the connection more secure as compared to previous secure protocols WEP and WPA.
WPA2 has personal and enterprise options, making it ideal for home users and businesses. However, it needs a significant amount of processing power so if you have an old device, it may be slow or not work at all.
Besides what security protocol you use, it is important to secure your wifi with a strong network security key AKA password. It is suggested to update the device and use the latest security encryption protocol to ensure maximum security of the network.
Frequently Asked Question
Which is better WEP WPA or WPA2?
WPA2 is the second version of the WPA standard. Using some encryption is always better than using none, but WEP is the least secure of these standards, and you should not use it if you can avoid it. WPA2 is the most secure of the three.
What security should I use WEP WPA WPA2 or WPA3?
WPA3 provides extra security and encryption if you compare it with its previous versions, such as WPA2, WPA, and WEP. With WPA3, all the traffic between you and the other end will be encrypted until the other end is authenticated.
Is WEP faster than WPA2?
WPA2 is the fastest of the security protocols, while WEP is the slowest. The network speed, it depends on the bandwidth and other factors.
Final Words:
Wireless security is a crucial aspect of staying safe online. Connecting to the internet over insecure links or networks is a security risk that could potentially lead to data loss, leaked account credentials, and the installation of malware on your network. Using the proper Wi-Fi security measures is critical – but in doing so, it’s important to understand the differences between different wireless encryption standards, including WEP, WPA, WPA2, and WPA3.
WHAT TO READ NEXT?